Lavanya
Feb 13, 2026
The EU Cyber Resilience Act (CRA) introduces cybersecurity obligations that extend beyond traditional IT security teams. Unlike regulations that target single departments, the Cyber Resilience Act and product compliance requirements demand coordination between engineering, compliance, supply chain, and quality assurance functions throughout the product lifecycle.
Manufacturers accustomed to managing chemical compliance under REACH or RoHS now face parallel cybersecurity documentation standards. Products with digital elements must demonstrate vulnerability management, secure development practices, and continuous monitoring before entering EU markets after December 11, 2027.
This article examines how cybersecurity compliance for manufacturers intersects with existing regulatory frameworks, the operational challenges of cross-functional coordination, and how enterprises can implement systems that address both cyber resilience and material substance obligations.
Table of Contents
Understanding CRA's Cross-Functional Impact
Core Requirements and Product Classifications
Documentation and Vulnerability Management Challenges
Supply Chain Integration and Supplier Requirements
Enforcement Timeline and Penalty Structure
Building Integrated Compliance Capabilities
Frequently Asked Questions
Understanding CRA's Cross-Functional Impact
The Cyber Resilience Act establishes mandatory cybersecurity standards for products with digital elements sold in the European Union. Published in the Official Journal on December 10, 2024, the regulation becomes fully applicable 36 months later, creating a December 11, 2027 compliance deadline.
Why Engineering-Compliance Collaboration Is Mandatory
Engineering teams designing connected devices, embedded software, and IoT systems must work alongside compliance professionals who manage PFAS restrictions and microplastics bans. This convergence creates operational complexity that cannot be addressed through departmental silos.
Engineering and compliance collaboration becomes mandatory because CRA obligations span product design, component selection, supplier assessments, vulnerability tracking, and post-market surveillance. Organizations that separate these functions face documentation gaps, audit failures, and potential market access delays.
Industries and Products Affected
The Cyber Resilience Act scope extends across consumer electronics, industrial automation, building management systems, and connected devices. Products previously subject only to RoHS material restrictions and electrical safety standards now require cybersecurity documentation.
Industrial control systems, programmable logic controllers, and manufacturing execution systems require cybersecurity compliance for manufacturers operating in critical infrastructure sectors. Software developers must implement secure development lifecycles and provide security updates comparable to hardware manufacturers' obligations.
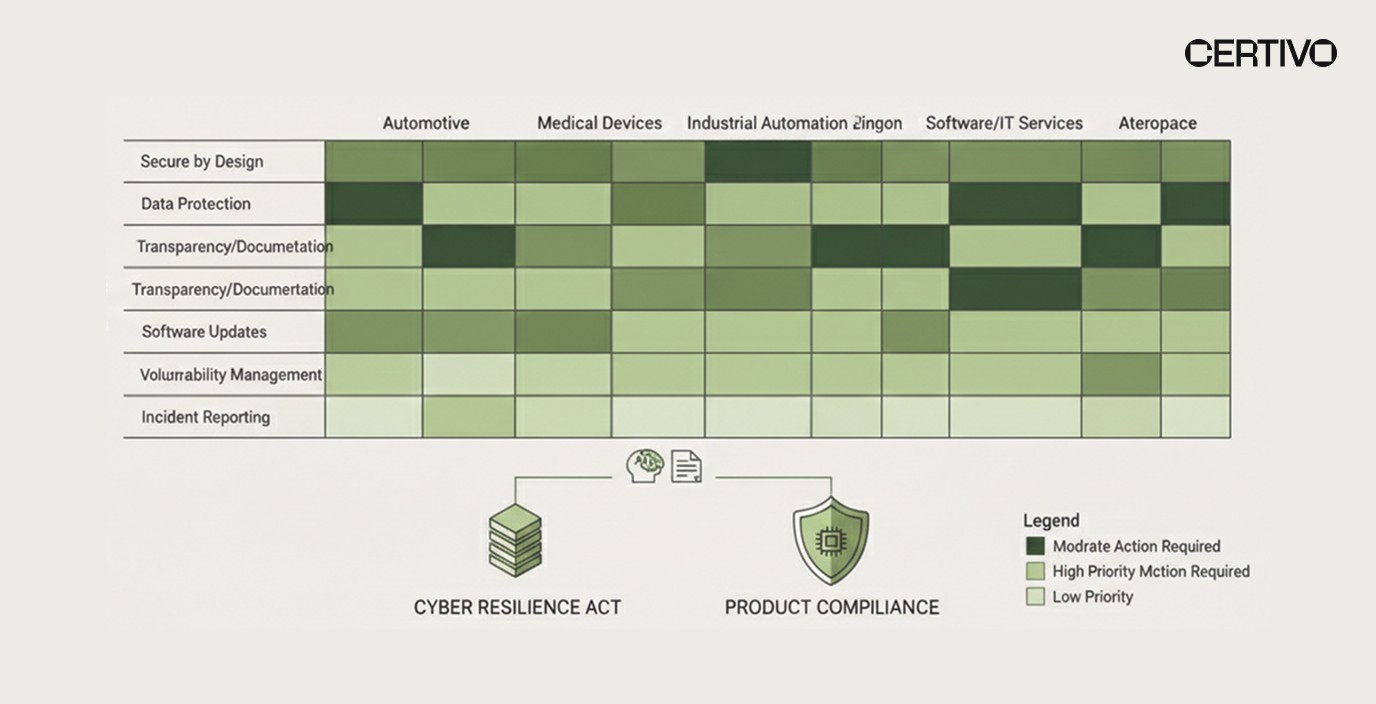
Core Requirements and Product Classifications
Essential Cybersecurity Requirements
CRA imposes specific obligations at each product lifecycle stage. Product cybersecurity requirements include secure development practices, vulnerability handling processes, and continuous security updates for a defined support period.
Products must be designed to minimize attack surfaces, prevent unauthorized access, and protect data confidentiality and integrity. Engineering teams must implement security by default, ensuring products ship in the most secure configuration without requiring user intervention.
Manufacturers must establish vulnerability management protocols requiring coordination between development teams creating patches and compliance teams documenting remediation timelines. Products must receive security updates for their expected operational lifetime or a minimum of five years from market placement.
Risk Classification Framework
The regulation categorizes products into default, Class I, and Class II classifications based on functionality and potential impact. Class I products include password managers and network management tools requiring third-party conformity assessment. Class II encompasses operating systems, public key infrastructure components, and microprocessors.
Engineering and compliance teams must evaluate product classifications during design phases, not after development completion. Classification determines conformity routes, testing requirements, and documentation depth, directly impacting project timelines and resource allocation.
Technical documentation requirements parallel those under CE marking frameworks. Manufacturers must maintain records demonstrating conformity with essential cybersecurity requirements for ten years after product discontinuation.
Documentation and Vulnerability Management Challenges
Technical Documentation Requirements
Implementing Cyber Resilience Act and product compliance requirements creates documentation burdens comparable to those under PFAS reporting and substance restriction frameworks. Organizations must maintain technical documentation, EU declarations of conformity, and vulnerability records across product portfolios.
Manufacturers must compile comprehensive technical files demonstrating conformity with essential cybersecurity requirements. Documentation includes product descriptions, risk assessments, security architecture specifications, and test reports. This material must remain current throughout the product lifecycle.
Continuous audit-ready documentation becomes necessary because authorities can request access at any point during or after market placement. Organizations maintaining compliance documentation for chemical substances and safety testing must extend those systems to accommodate cybersecurity records.
Vulnerability Tracking and Disclosure
The regulation requires manufacturers to establish processes for receiving, tracking, and addressing vulnerability reports. Organizations must maintain vulnerability databases, assess severity using standardized scoring systems, and communicate remediation timelines to affected parties.
Engineering and compliance collaboration proves essential because technical teams identify and patch vulnerabilities while regulatory functions handle disclosure obligations. Companies managing supplier compliance portals for material declarations can implement similar frameworks for vulnerability disclosure.
Software Bill of Materials Requirements
CRA introduces Software Bill of Materials (SBOM) requirements for Class I and Class II products. Organizations must document all software components, including third-party libraries, open-source packages, and firmware dependencies.
BOM-level compliance intelligence systems that track material composition at component level provide architectural foundations for SBOM management. Companies using BOM-level material mapping for substance compliance can extend those capabilities to capture software dependencies.
Supply Chain Integration and Supplier Requirements
Component-Level Security Verification
The Cyber Resilience Act supply chain requirements create obligations extending beyond internal functions. Manufacturers must verify component security, assess supplier capabilities, and maintain traceability records demonstrating conformity throughout multi-tier supply networks.
Organizations purchasing semiconductors, wireless modules, and software libraries must verify those components meet cybersecurity requirements before integration. This verification parallels substance compliance screening that manufacturers perform for REACH restricted substances.
Multi-tier supply chain transparency requirements demand visibility into component origins, security testing procedures, and vulnerability management processes. Companies implementing supplier risk scoring for material compliance can extend those frameworks to evaluate cybersecurity capabilities.
Supplier Data Collection Workflows
Manufacturers must collect security attestations, vulnerability disclosure policies, and support commitment statements from component suppliers. Standardized supplier questionnaire frameworks that currently gather material declarations can incorporate cybersecurity questions.
Supplier self-service portals enable component manufacturers to upload conformity declarations, security certificates, and vulnerability bulletins directly into downstream manufacturers' compliance systems. This approach eliminates manual data entry and reduces declaration errors.
Organizations managing both chemical compliance and cybersecurity requirements cannot operate separate supplier engagement processes without creating redundancy. Integrated approaches that collect material and security data through unified portals improve response rates and data quality.
Production System Integration
Cybersecurity conformity verification must integrate into existing quality management systems and production workflows. Organizations performing incoming inspection for material composition must add cybersecurity documentation verification to those procedures.
Design-for-compliance PLM workflows enable engineering teams to evaluate cybersecurity requirements during component selection and design phases. Systems that currently flag restricted substances during product development can provide similar notifications when components lack necessary cybersecurity certifications.
Enforcement Timeline and Penalty Structure
Critical Implementation Milestones
The CRA compliance timeline follows a phased approach with the primary enforcement date of December 11, 2027. Notification requirements for critical Class II products begin September 11, 2026, requiring affected manufacturers to submit documentation earlier.
Reporting obligations for actively exploited vulnerabilities and severe incidents commence 21 months after entry into force. Manufacturers must establish vulnerability reporting channels and incident notification procedures before this deadline.
Organizations planning product launches in late 2027 must complete conformity assessments months in advance to avoid market access delays. Companies managing REACH regulatory updates require similar monitoring systems for CRA implementation guidance.
Financial Penalties and Market Access Restrictions
The Cyber Resilience Act enforcement framework establishes administrative fines comparable to those under GDPR. Maximum penalties reach €15 million or 2.5% of total worldwide annual turnover, whichever proves higher.
Non-compliant products cannot be placed on EU markets after the enforcement date. Market surveillance authorities can order product recalls, prohibit future sales, and impose interim measures while investigating potential violations.
Product compliance risks under CRA parallel those under REACH substance restrictions. Companies managing regulatory risk across multiple frameworks must implement unified monitoring systems that track obligation deadlines and enforcement developments.
Liability Across Distribution Chains
Importers placing products on EU markets assume compliance obligations when manufacturers lack EU establishment. This liability structure affects distribution agreements, requiring contract provisions addressing cybersecurity conformity and documentation provision.
Distributors must verify manufacturers or importers have completed conformity assessment procedures before making products available. Enterprise customers increasingly require cybersecurity compliance verification before procurement decisions.
Customer trust centers that provide self-service access to regulatory documentation help organizations demonstrate conformity. Companies operating customer trust portals for substance declarations can expand those platforms to include cybersecurity conformity certificates.
Building Integrated Compliance Capabilities
Strategic Preparation Framework
Organizations preparing for Cyber Resilience Act enforcement require systematic approaches addressing technical, operational, and organizational readiness. Conduct comprehensive product portfolio reviews identifying which items meet CRA definitions of products with digital elements.
Classify applicable products into default, Class I, or Class II categories based on functionality and risk criteria. Evaluate existing cybersecurity practices against essential requirements outlined in CRA annexes. Identify gaps in secure development practices, vulnerability management procedures, and security update delivery mechanisms.
Establish documentation systems capturing security design decisions, component selections, testing results, and conformity assessment evidence. Implement version control ensuring documentation remains current throughout product lifecycles.
Cross-Functional Process Integration
Engineering and compliance collaboration requires shared tooling, common terminology, and aligned incentive structures. Organizations that implement integrated PLM ERP compliance systems break down information silos while maintaining role-appropriate access controls.
Establish governance structures connecting engineering, compliance, quality, supply chain, and legal functions. Define decision-making authorities for classification determinations, conformity route selections, and security update prioritization.
Create communication protocols ensuring vulnerability information reaches appropriate functions for remediation and disclosure. Integrate vulnerability tracking with existing quality management systems and customer support platforms.
AI-Powered Compliance Automation
AI-native compliance automation capabilities address the scale and complexity challenges inherent in managing Cyber Resilience Act and product compliance obligations across extensive product portfolios. Organizations cannot manually track vulnerabilities, maintain current documentation, and coordinate cross-functional workflows without intelligent automation.
CORA-powered regulatory intelligence continuously monitors vulnerability databases, security advisories, and component manufacturer notifications. When new vulnerabilities emerge affecting components used in finished products, CORA intelligence identifies affected SKUs and assesses severity based on product usage context.
CORA intelligence maintains documentation currency as products undergo design changes, component substitutions, and security updates. When engineering teams modify product specifications, CORA-enabled analysis identifies affected compliance documents and generates updated versions.
Cross-Regulation Integration
Products simultaneously subject to REACH substance restrictions, RoHS material limits, and CRA cybersecurity requirements require integrated compliance management. CORA-driven compliance intelligence maps obligations across regulations, identifying products requiring action under multiple frameworks.
End-to-end product compliance approaches address full product lifecycles from design through post-market surveillance, creating unified records accessible to all stakeholder functions. Companies implementing continuous audit-ready documentation systems position themselves for efficient conformity demonstration.
The December 11, 2027 enforcement deadline provides time for systematic preparation when organizations begin implementation activities during 2025. Companies delaying until 2026 face compressed timelines affecting new product launches and potentially requiring market access delays.
Explore how Certivo supports continuous compliance readiness across cybersecurity, chemical, and environmental regulations through integrated compliance intelligence and cross-functional collaboration tools.
Frequently Asked Questions
How can companies reduce compliance-related delays in product launches?
End-to-end product compliance systems integrating cybersecurity documentation with material declarations eliminate sequential compliance reviews. Organizations using integrated PLM ERP compliance platforms enable parallel conformity verification across regulatory domains, reducing time between design completion and market readiness.
How can companies maintain continuous compliance after product launch?
Continuous audit-ready documentation requires automated monitoring of regulatory changes, vulnerability disclosures, and component updates. CORA-powered regulatory intelligence identifies products affected by new obligations or emerging security issues, generating remediation workflows that maintain conformity throughout product lifecycles.
How can compliance data be shared securely with customers and regulators?
Customer trust centers provide controlled access to conformity certificates, vulnerability disclosures, and substance declarations without email distribution. Organizations operating customer trust portals enable self-service compliance documentation access while maintaining security and version control.
What documentation must manufacturers maintain for CRA conformity?
Technical files must include product descriptions, security risk assessments, test reports, and conformity assessment procedures. Organizations must retain these records for ten years after discontinuing products. Continuous audit-ready documentation systems ensure current evidence remains accessible to authorities.
How does CRA interact with existing product compliance requirements?
Products subject to REACH restrictions, RoHS limits, and cybersecurity requirements must demonstrate conformity under all applicable frameworks. AI-native compliance automation maps cross-regulation obligations, preventing gaps where teams address one requirement while overlooking parallel obligations.
Lavanya
Lavanya is an accomplished Product Compliance Engineer with over four years of expertise in global environmental and regulatory frameworks, including REACH, RoHS, Proposition 65, POPs, TSCA, PFAS, CMRT, FMD, and IMDS. A graduate in Chemical Engineering from the KLE Institute, she combines strong technical knowledge with practical compliance management skills across diverse and complex product portfolios.
She has extensive experience in product compliance engineering, ensuring that materials, components, and finished goods consistently meet evolving international regulatory requirements. Her expertise spans BOM analysis, material risk assessments, supplier declaration management, and test report validation to guarantee conformity. Lavanya also plays a key role in design-for-compliance initiatives, guiding engineering teams on regulatory considerations early in the product lifecycle to reduce risks and streamline market access.
Her contributions further extend to compliance documentation, certification readiness, and preparation of customer deliverables, ensuring transparency and accuracy for global stakeholders. She is adept at leveraging compliance tools and databases to efficiently track regulatory changes and implement proactive risk mitigation strategies.
Recognized for her attention to detail, regulatory foresight, and collaborative approach, Lavanya contributes significantly to maintaining product compliance, safeguarding brand integrity, and advancing sustainability goals within dynamic, globally integrated manufacturing environments.

